Low power consumption and high reliability
The blockchain technology we use is based on processes of low energy consumption and high reliability such as platforms based on “Proof of Stake (PoS)” or Proof of Participation in the evolved network of Ethereum 2.0


The immutability of Non Fungible Tokens
NFTs are tokens used to represent ownership of unique items. NFTs allow their creators to tokenize things like art, collectibles, or even real estate. They are secured by the Ethereum blockchain and can only have one official owner at a time.
The cost of transactions is reduced since it does not require intermediaries.
We use efficient technology
The technology based on Proof of Stake (PoS) allows to save a lot of energy compared to other blockchain platforms based on the previous Proof of Work (PoW).
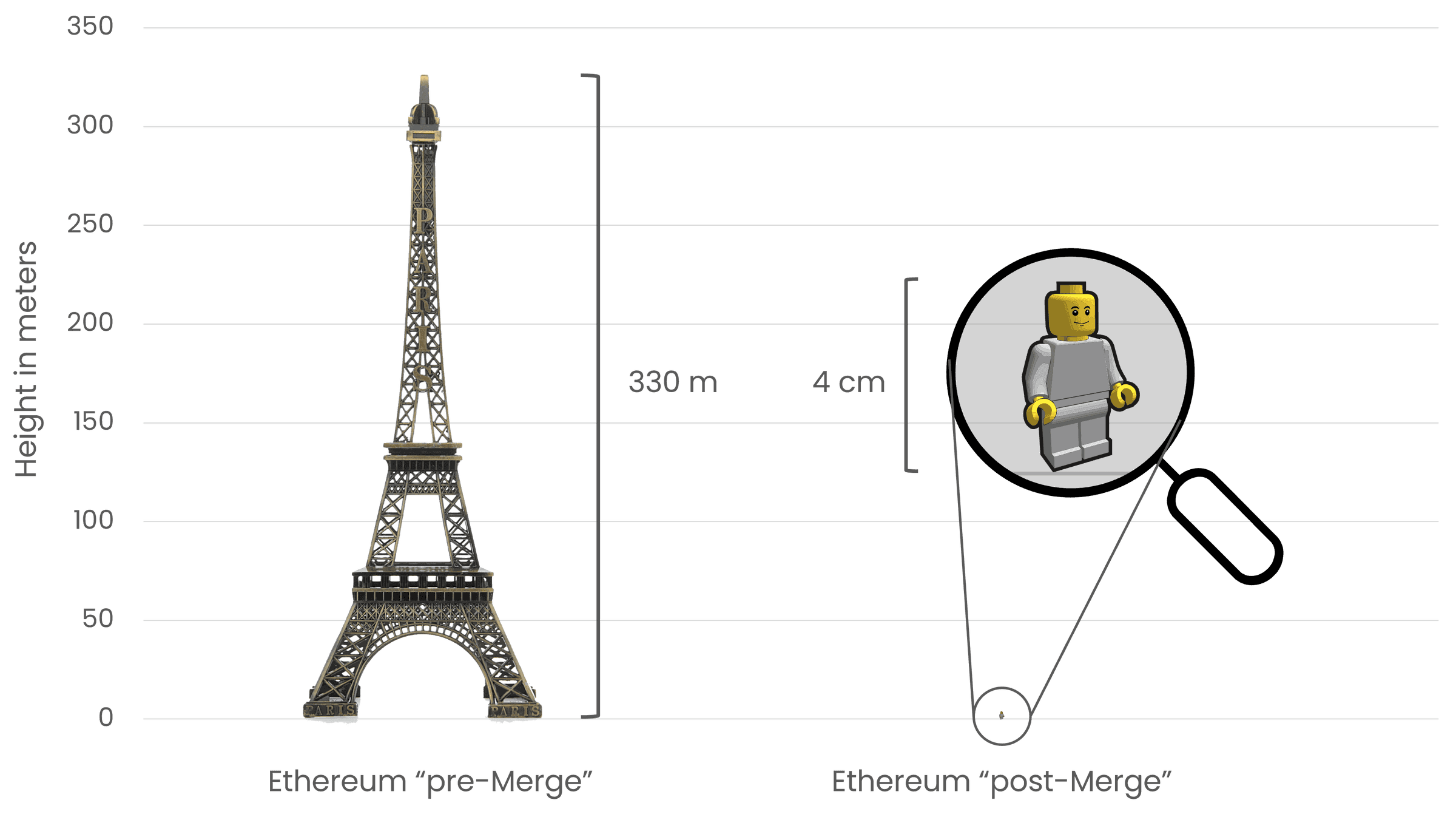
Ethereum is a green blockchain. Ethereum’s proof-of-stake consensus mechanism uses ETH instead of power to protect the network. Ethereum’s energy consumption is approximately ~0.0026 TWh/year across the entire global network.
Read more…

Why GTIME Blockchain?
We are the first to implement specific energy traceability projects
Since 2016, we have been part of various pilot projects of public and private interest. In 2018 we created the first information traceability platform, mining the first 1000 GWh with GTIME® Blockchain.
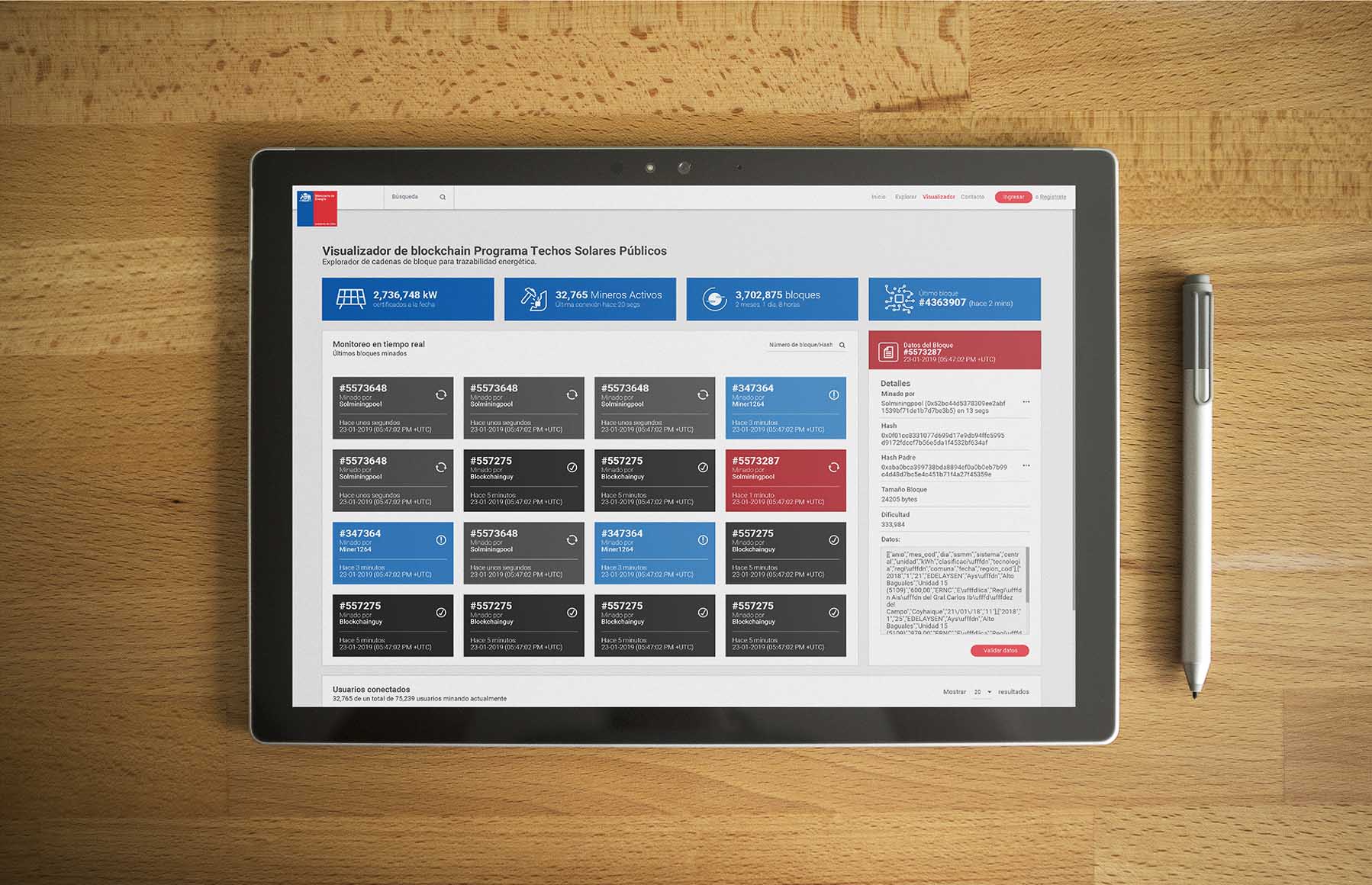
Our traceability platform has participated in projects of public interest with financing from the World Bank, allowing the tracing of solar energy data from the photovoltaic installations of the Public Solar Roofs program. On our blog, more projects are shown where our technology has been implemented and tested.
Learn about blockchain and NFT’s technology
Frequent questions
What is blockchain?
Blockchain is a distributed ledger technology used to maintain a secure and transparent record of transactions and data online. It is characterized by its block chain structure, where each block contains a set of transactions or data and is sequentially linked to the previous block, thus creating a continuous chain of blocks. Here are some key features of the blockchain:
1. **Decentralization**: Unlike traditional centralized systems, such as banks or servers, in blockchain there is no central entity that controls the network. Instead, the information is stored and verified in a decentralized manner across multiple nodes in the network.
2. **Security**: The data stored in a blockchain is highly secure and difficult to modify due to the cryptography used in the technology. Each block is linked to the previous one via a hash function, making manipulation of one block virtually impossible without changing all subsequent blocks.
3. **Transparency and trust**: The information on a blockchain is public and accessible to anyone who wants to verify it. This creates a high level of transparency and trust in transactions and records.
4. **Immutability**: Once information is added to a blockchain, it is extremely difficult to remove or modify it. This is useful in applications where data integrity is essential.
5. **Smart Contracts**: Some blockchains, such as Ethereum, allow the execution of smart contracts, which are autonomous computer programs that are executed when certain predefined conditions are met. This has applications in fields like finance, supply chain management, and more.
6. **Cryptocurrencies**: Most people are aware of blockchain through its association with cryptocurrencies like Bitcoin. Cryptocurrencies are digital assets that use the blockchain to securely record and verify transactions.
The use of blockchain has extended beyond cryptocurrencies and is applied in various industries, including medical records management, product traceability, electronic voting, digital asset management, and much more. Technology continues to evolve and find new applications in the real world.
Why is blockchain technology secure?
Blockchain technology is secure due to several key features that make it resistant to tampering and ensure data integrity. Here are some reasons why blockchain is considered a secure technology:
1. **Advanced Cryptography**: On a blockchain, information is stored securely using advanced cryptographic techniques. Each block contains a hash of the previous block, and this creates a chain of interconnected blocks. Any attempt to modify one block would require modifying all subsequent blocks, which is extremely difficult due to cryptography.
2. **Decentralization**: Unlike centralized systems that have a single point of failure, blockchain is a decentralized network of nodes (computers) that store and verify information. To modify the data on the chain, an attacker would have to take control of most nodes on the network, which is highly unlikely in well-established and secure blockchain networks.
3. **Consensus**: Blockchains use consensus algorithms to validate and confirm transactions. For example, in the case of Bitcoin, the Proof of Work (PoW) algorithm is used. Network nodes compete to solve complex math problems to add a new block to the chain. This consensus process ensures that only valid transactions are added to the chain.
4. **Immutability**: Once information is added to a block and committed to the chain, it is virtually impossible to change or remove it. This is due to the nature of cryptography and the way the blocks are linked together.
5. **Transparency**: The information in a blockchain is public and transparent. Anyone can verify the transactions and data stored on the chain. This fosters trust and accountability.
6. **Security Against Cyber Attacks**: Since information is stored decentrally in multiple locations and is protected by cryptography, it is more difficult for cyber attackers to compromise the security of a blockchain.
While blockchain is a secure technology, it is not immune to all risks. For example, 51% attacks (when one group controls more than 50% of the network’s computing power) and double-spend attacks are possible on some blockchain networks. Furthermore, the security of a blockchain largely depends on its specific implementation and configuration. Therefore, it is important to adopt good security practices when designing and using blockchain-based systems.
Who validates the traceability information and certificates?
Validation of traceability information and certificates on a blockchain is typically the responsibility of multiple actors in the network, and is highly dependent on the specific design and implementation of the system. The possible actors involved in this process are described below:
1. **Network nodes**: In a blockchain, the nodes are the computers that are part of the network and maintain a copy of the entire blockchain. The nodes play a fundamental role in validating the information. Every time a transaction is made or new data is recorded on the blockchain, the nodes work together to verify and validate the information before adding it to the blockchain. This is done through consensus algorithms, such as Proof-of-Work (PoW) or Proof-of-Stake (PoS), depending on the blockchain.
2. **Miners or Validators**: In some blockchains, such as Ethereum, the nodes involved in validating transactions are known as “miners” or “validators”. These nodes compete to solve complex math problems or perform specific tasks to add new blocks to the blockchain. This validation process is part of the blockchain’s consensus mechanism and ensures that only valid transactions are included in the blockchain.
3. **Certificate Authorities or Entities**: In some cases, especially in business or government applications, there may be certifying authorities or entities that issue digital certificates or validate information before it is recorded on the blockchain. These entities may be in charge of verifying the authenticity of the information and issuing certificates that are then recorded in the blockchain.
4. **Users and stakeholders**: In some blockchain-based traceability systems, users and stakeholders may also play a role in validation. They can verify information and certificates using public keys or blockchain query tools to make sure the information is accurate.
In short, the validation of traceability information and certificates on a blockchain is a collaborative process in which multiple actors work together to ensure the integrity and accuracy of the data recorded on the chain. The way in which this validation is carried out can vary depending on the blockchain and the specific application.
How much energy is used in traceability with Ethereum 2.0?
The transition to Ethereum 2.0 aims to significantly reduce power consumption compared to the previous version of Ethereum, which used a power-intensive Proof-of-Work (PoW) consensus mechanism. Ethereum 2.0 adopts a consensus mechanism called Proof-of-Stake (PoS), which is much more energy efficient.
In PoW, miners compete to solve complex mathematical problems, which requires a significant amount of computing power and therefore consumes a large amount of electrical energy. In contrast, in PoS, validators participate in confirming transactions and creating new blocks based on the amount of cryptocurrency they are willing to “stake” as collateral. High power consumption is not necessary to solve mathematical problems in PoS, since the selection of validators is based on their participation in the network.
While it is difficult to provide an exact figure for the power savings in Ethereum 2.0 compared to Ethereum 1.0, it is expected to be considerable. The transition to Ethereum 2.0 is a response to concerns about energy consumption and environmental sustainability associated with PoW.
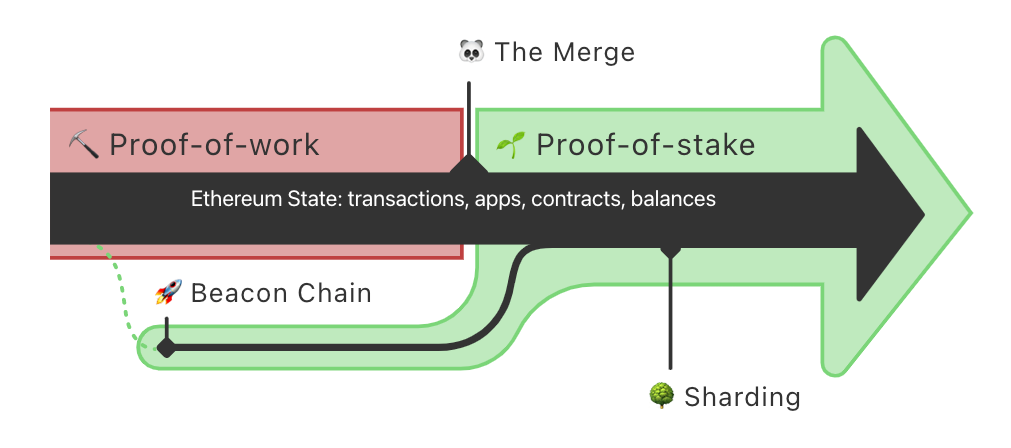
It is important to note that Ethereum 2.0 is being rolled out in phases, and the full transition will take some time. However, PoS adoption has already started with the Beacon Chain, which is a parallel network running on PoS and has been up and running since December 2020. As Ethereum 2.0 fully rolls out, its carbon footprint and their power consumption are significantly lower compared to the original Ethereum network.
What is Proof of Work and Proof of Stake?
Proof-of-Work (PoW) and Proof-of-Stake (PoS) are two consensus mechanisms used on blockchain, including Ethereum, to validate transactions, create new blocks on the chain, and ensure network security. Here is an explanation of each one in relation to Ethereum:
1. **Proof of Work (PoW)**:
– **How it works**: In a PoW system, like the one used in Ethereum before the transition to Ethereum 2.0, network nodes (called miners) compete to solve complex mathematical problems. The first node to solve the problem has the right to create a new block and add it to the blockchain.
– **Power Consumption**: PoW requires a large amount of computing power and therefore consumes a lot of electrical power. Miners must invest in specialized hardware (such as ASICs) and consume electricity to participate in mining.
– **Security**: PoW is highly secure due to the difficulty of solving the math problems, which makes it costly and computationally intensive to carry out an attack.
2. **Proof of Stake (PoS)**:
– **How it works**: In a PoS system, such as the one implemented in Ethereum 2.0, nodes (called validators) participate in confirming transactions and creating new blocks based on the amount of cryptocurrencies that are available to “bet” or block as collateral. Validators are chosen to propose and validate blocks in proportion to their participation in the network.
– **Power Consumption**: PoS is much more energy efficient than PoW, as it does not require solving complex math problems. There is no constant energy-consuming mining competition.
– **Security**: PoS is based on economic participation and betting as collateral. Validators have a financial incentive to act honestly, as they may lose some or all of their collateral if they are identified as malicious.
Ethereum 2.0 is in the process of migrating from PoW to PoS as its primary consensus mechanism to address power consumption and scalability issues associated with PoW. The transition to PoS is taking place in several phases, and Ethereum is expected to become more energy efficient once the migration is complete. The Beacon Chain, which runs on PoS, is already up and running as part of Ethereum 2.0, and the full switch to PoS is expected to happen gradually in later phases of the Ethereum 2.0 upgrade.
What is the ERC1155 standard?
A standard interface for contracts that manage multiple token types. A single deployed contract may include any combination of fungible tokens, non-fungible tokens or other configurations (e.g. semi-fungible tokens).
What is meant by Multi-Token Standard?
The idea is simple and seeks to create a smart contract interface that can represent and control any number of fungible and non-fungible token types. In this way, the ERC-1155 token can do the same functions as an ERC-20 and ERC-721 token, and even both at the same time. It improves the functionality of both the ERC-20 and ERC-721 standards, making it more efficient and correcting obvious implementation errors.
The ERC-1155 token is described fully in EIP-1155
What does IPFS mean?
IPFS stands for “Interplanetary File System” in English, and is a peer-to-peer network and protocol designed to create a more decentralized and resilient way of storing and sharing information on the web. It was developed by Juan Benet and launched in 2015.
Instead of relying on centralized server locations to store and deliver data, IPFS uses a distributed approach in which data is broken up into small chunks and stored on network nodes. Each data chunk is identified by a unique cryptographic hash, allowing for easy data retrieval over the network. Here are some key features and concepts of IPFS:
1. **Decentralized Distribution**: Data in IPFS is stored in a distributed manner across multiple nodes instead of relying on a centralized server. This improves resistance to censorship and the availability of information.
2. **Unique Identifiers**: Each chunk of data is identified by a unique hash, which ensures data integrity and allows for easy recovery.
3. **Local Cache**: IPFS uses a local cache on the nodes to store frequently accessed chunks of data. This improves the speed of data access and reduces the need to make multiple requests over the network.
4. **Content instead of location**: In IPFS, data is routed based on its content instead of its physical location. This means that the same content can be available at multiple node locations, reducing network congestion and improving efficiency.
5. **Incentives and Rewards**: IPFS introduces concepts of incentives and rewards to motivate users to share and maintain data on the network. This may include token systems and rewards for data storage and delivery.
6. **Decentralized Applications (DApps)**: IPFS is commonly used in combination with blockchain technologies to create decentralized applications (DApps) that store and distribute data in a decentralized manner.
IPFS is a technology that has gained popularity in the blockchain and decentralization community due to its potential to create a more decentralized and censorship-resistant web. It allows the creation of applications and services that do not depend on central servers and that can work efficiently in distributed networks.
Add value to your products and services with blockchain
Describe your products or services to us to help you incorporate information into a digital certificate that allows you to add value and increase the interest of your customers throughout your value chain.
GTIME® Blockchain
We work to make information transparent and make products and services truly sustainable.
